| A comprehensive risk analysis is the cornerstone of HIPAA compliance. Many organizations overlook this step, leading to vulnerabilities in their data protection strategies. Learn more here: https://data-guard365.com/articles/top-hipaa-violations-and-how-to-avoid-them/ |
Top HIPAA Violations and How to Avoid Them


Written by
PrimaryChipmunk
431 days ago
Related articles:
IoT in Remote Patient Monitoring: Building Connected Healthcare Ecosystems
The integration of IoT into remote patient monitoring is redefining how healthcare is delivered, shifting the industry from reactive treatment models to proactive, connected care ecosystems. By enabling continuous data..
Saudi Arabia Remote Patient Monitoring System Market Strategic Analysis: Growth Forecast and Competition 2027
MarkNtel Advisors Research Analyses that Saudi Arabia Remote Patient Monitoring System Market is projected to grow at a CAGR of around 18% during the forecast period, i.e., 2022-27. Which are..
Enhancing Healthcare Communication with Patient Display Boards and Digital Notice Boards
In today’s fast-paced healthcare environment, effective communication plays a pivotal role in delivering quality care and improving patient satisfaction. The rise of patient display boards and digital notice boards represents..
Privacy and security in healthcare: A must-read for healthtech entrepreneurs
Ensuring Security in Healthcare AppsWith the rise of cyberattacks on healthcare data, protecting sensitive patient information has never been more critical. Compliance with privacy regulations such as HIPAA and GDPR..
Global Patient Data Management Systems (PDMS) Market Size, Share & Trends Analysis 2025-2033
Patient Data Management Systems (PDMS) Market Analysis 2025-2033The Global Patient Data Management Systems (PDMS) Market report provides information about the Global industry, including valuable facts and figures. This research study..
Patient Engagement Software
Patient Engagement Software at Daffodil Development Company
About Daffodil Software Development Company:Daffodil Software is a leading software development company specializing in creating innovative and effective healthcare solutions, including patient engagement..
Patient Engagement Software
Patient Engagement Software at Daffodil Development Company
About Us:Daffodil Software Development Company is at the forefront of healthcare technology, specializing in the development of innovative patient engagement software. Our solutions..
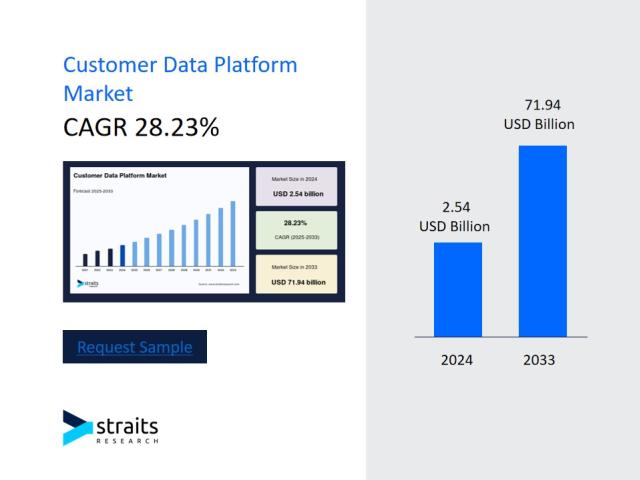
The Single Source of Truth: How Customer Data Platforms are Unifying the Corporate World
The modern customer journey is a complex web of interactions across websites, mobile apps, social media, email, and physical stores. For years, businesses have struggled to piece together these fragmented..
Mastering Data Engineering Service for Cloud Success
In today’s data-driven world, companies are swimming in an ocean of information. Yet, without the right tools and infrastructure, that data remains untapped potential. That’s where Data Engineering Service comes..
How AI Is Transforming the Work of Data Analysts
Artificial Intelligence (AI) is rapidly reshaping industries, and the field of data analysis is no exception. As AI technologies become more powerful and accessible, the role of data analysts is..
What’s the Role of APIs in Data Analytics?
IntroductionImagine you open your favorite ride-sharing app. You check the estimated fare, track the driver’s location, and see the trip summary in real time. Ever wondered how all that information..
Data Loss Prevention Market Market Growth, CAGR, Size, Share, and Forecast to 2033
Data Loss Prevention Market Synopsis 2025:
The Data Loss Prevention Report offers an in-depth overview of this industry, summarizing essential findings such as market size, growth forecasts, and key trends...
How to Use Data Analytics to Optimize Your Marketing Campaigns
In the rapidly evolving world of digital marketing, data analytics has become an essential tool for marketers seeking to optimize their campaigns. By harnessing the power of data, businesses can..
Statistics for Data Analytics: Concepts & Practices
Data analytics is a critical field that helps organizations make data-driven decisions by uncovering trends, patterns, and insights. To make sense of the vast amount of data collected, statisticians and..
How Big Data is Transforming the Startup Landscape
Big Data has emerged nowadays as a powerful ally for startups. It enables businesses to make smarter decisions, optimize operations, and tailor services to customer needs. This transformative technology isn’t..
From Insights to Action: How Data Transforms Marketing Strategies
In today’s digital landscape, data has become a pivotal
force in shaping the future of marketing. Businesses are increasingly relying
on Martech tools to
gather, analyze, and transform data into..
The Role of Data in Shaping Modern Marketing Strategies
In today's evolving digital landscape, Martech (marketing technology)
plays a crucial role in enabling businesses to leverage the full potential of
data. This tech article explores
how data is reshaping..
Top Python Security Practices Every Business Should Follow in 2026
Python remains one of the most popular programming languages worldwide, powering AI solutions, automation tools, SaaS platforms, and API-driven applications. However, as its adoption grows, so does the risk of..